Combining quantum-inspired keying, AI-driven smart compression, and noise-adaptive embedding for robust, low-detectability covert channels
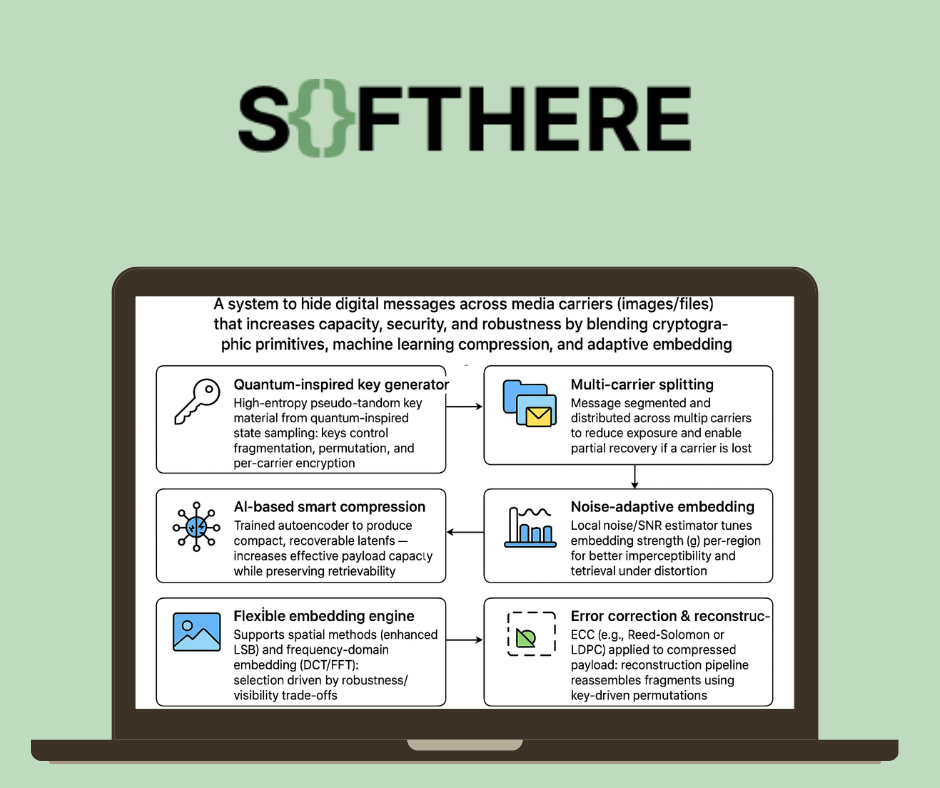
A system to hide digital messages across media carriers (images/files) that increases capacity, security, and robustness by blending cryptographic primitives, machine learning compression, and adaptive embedding. Core components:
Quantum-inspired key generator
High-entropy pseudo-random key material from quantum-inspired state sampling; keys control fragmentation, permutation, and per-carrier encryption.
Multi-carrier splitting
Message segmented and distributed across multiple carriers to reduce exposure and enable partial recovery if a carrier is lost.
AI-based smart compression
Trained autoencoder to produce compact, recoverable latents — increases effective payload capacity while preserving retrievability.
Noise-adaptive embedding
Local noise/SNR estimator tunes embedding strength (α) per-region for better imperceptibility and retrieval under distortion.
Flexible embedding engine
Supports spatial methods (enhanced LSB) and frequency-domain embedding (DCT/FFT); selection driven by robustness/visibility tradeoffs.
Error correction & reconstruction
ECC (e.g., Reed-Solomon or LDPC) applied to compressed payload; reconstruction pipeline reassembles fragments using key-driven permutations.
Losses & training
Composite loss: perceptual/image loss (MSE/Perceptual) + message loss (BCE/BER-aware). Train on datasets augmented with JPEG, noise, rescaling, etc.
Evaluation metrics
PSNR / SSIM for carrier quality; BER and F1 for payload recovery; adversarial tests: JPEG compression, Gaussian noise, rescaling, and steganalysis tools.
Implementation stack
PyTorch or TensorFlow for ML components; optional quantum simulators (Qiskit) for keygen; GPU acceleration recommended.
Operational & security notes
Tunable knobs: compression ratio, α, number of carriers. Trade-off between capacity, detectability, and compute cost. Distribution + encryption minimize full-message leakage if a subset of carriers is compromised